Don't miss the chance to work with top 1% of developers.
Sign Up Now and Get FREE CTO-level Consultation.
Confused about your business model?
Request a FREE Business Plan.
How to Ensure Mobile App Security While Developing for Android and iOS?
Table of contents

A long time ago, we were afraid of burglars stealing money from our homes. To prevent the same, we used to lock our houses using the safest locks. But, nowadays, these locks are of no use.
Why? Because those burglars have become smarter now. They have acquired a number of advanced stealing skills with two higher education degrees in the same. And they have also changed their names to Hackers from Burglars. These days, hackers do not attack your homes, instead, they attack your hand-held tiny devices using the applications installed in it.
Research says that hackers attack every 39 seconds, on average 2,244 times a day – that’s why mobile security is at the top of every organization’s worry and for all good reasons. If you are planning to develop your own app in the year 2020, you must pay heeds to mobile app security to avoid scams later.
A number of forward-thinking organizations are already doing this to protect their app’s data from breaches and cyber thefts. As per CyberCrime Magazine, global cybersecurity spending will exceed $1 trillion cumulatively from 2017 to 2021.
But, how can you safeguard your app to make your users believe that it is safe and secure? You will find the same in this blog. So, let’s dig in.
To start with, let’s look at the most common mobile app security mistakes that Android app developers New York often make while developing an app:
8 Development Mistakes That Plague Mobile App Security and Ways to Avoid Them

Application security is becoming challenging day by day with the multiplication of smartphones, mobile apps, and cloud-based solutions. But, because of several reasons, a number of times, mobile app developers fail to understand the importance of security in a mobile app and commit the following mistakes:
1. Weak Controls On the Server-Side
Any communication that occurs between the application and the users occurs via a server. As a result, servers are often the main targets of hackers.
The precautionary measures you can take to guarantee server-side security may range from employing a particular security expert in-house to just utilizing a testing device and playing it safe. The serious issue emerges when developers don’t pay heeds to server-side security considerations. Here are some basic reasons behind this:
- Small budget for security
- Excessive dependability on the mobile OS for security updates and obligation
- Developer having less security knowledge while working on a new language
- Vulnerabilities because of cross-platform development
There are certain precautions that developers can take while building mobile applications to prevent weak server-side controls. Now, let’s take a look at some of them:
- Scan Your Application: The best way to secure your mobile applications from server-side vulnerabilities is to scan them. You can scan your applications by using an automated scanner. An automated scanner detects basic issues that can be solved with a little effort of developers.
- Get a Detailed Manual Check: A number of automated security scanners report several vulnerabilities with some false negatives and false positives. So, it is crucial to look at them closely one by one with the help of a tester. This manual assessment is crucial to understand what threats are of low importance and what are of high importance.
- Use Secure Coding Practices: It doesn’t matter how many approaches you use to protect your app, if your code isn’t secure, nothing can stop your app from being insecure. It may take effort and time for implementing secure coding practices, but it will surely help you in the long run.
While that was all you can ensure on your end to build a secure app if you need advanced security than you can hire a cyber expert to assist you throughout the development procedure.
2. Lack of Secure Data Storage
Absence of secure data storage while building an app is yet another loophole when it comes to ensuring security. A typical practice among the app developers is to rely on the client storage for storing the data. However, client storage isn’t a sandbox environment where security ruptures are impractical. That means if the device is stolen or tampered with, there are chances of data being stolen.
The most ideal approach to secure your data storage across various platforms is to create an extra layer of encryption over the base level encryption given by the OS. This gives a massive lift to the mobile application’s security and reduces the app developer’s dependency on default encryption.
3. Insufficient Transport Layer Protection
The transport layer alludes to the route through which the information is transferred from the customer to the server and the other way around. Because of an insufficient transport layer, anybody can get to the data and steal it as per his/her will. This leads to identity threats and frauds.
A typical practice that developers use to prevent it is by using TLS and SSL to encrypt the communication. The problem arises because all SSLs aren’t the same. A number of these are issued by third-party companies or are self-marked. Here are a few different ways to secure mobile applications by fortifying the transport layer:
- Plan to make SSL chain verification mandatory.
- Do not expose the user’s session ID because of mixed SSL sessions.
- Alert the user if the mobile application identifies an invalid declaration.
- Use industry-standard cipher suites with proper key lengths because they are relatively stronger.
- Utilize the SSL of third-party companies, social networks, etc. when an app runs a routine via Webkit/browser.
- Try not to send sensitive information like passwords over alternate channels (e.g, MMS, SMS, or notifications).

4. Weak Encryption
App developers generally fail to utilize appropriate encryption controls that will shield data as it travels from the application to the server and the other way around. This failure puts the user’s data in danger of eavesdropping (a sort of hack called “man-in-the-middle). In the worst case, numerous application developers neglect to turn on a pop-up alert that will warn an application user if they’re in danger of eavesdropping.
Ensure your application utilizes Secure Sockets Layer (SSL) encryption between the server and the phone. Then ensure your developer tests the application to check whether it will quit working if an unapproved third-party (which is known as PROXY) is capturing the data.
5. No Binary Protections
If binary protection is missing, a hacker can easily reverse engineer the code of an application to infuse a malware in it. It a big concern as it can result in private data theft, revenue losses, and frauds.
To evade this, it is essential to utilize binary hardening techniques. Using it, the binary files are analyzed and altered to ensure against common exploits. This allows fixing of vulnerabilities in the legacy code itself without the requirement for source code. The application should also follow secure coding methods for checksum controls, jailbreak detection controls, and certificate pinning controls.
6. Unintended Data Leakage (UDL)
Unintended data leakage means the storage of application data on uncertain locations on the mobile which are insecure. The data is stored in such a location that is easily accessible by other users and apps.
This results in the breach of user protection prompting the unauthorized utilization of data. People often get confused between insecure data storage and unintended data leakage. However, they both are different. UDL is caused because of issues like Operating System bugs and carelessness of security in the system itself which are not in the hands of app developers.
While insecure data storage is caused by reasons which are completely in the hands of an app developer. You can prevent UDL by checking general leakage points, for example, logging, caching, application backgrounding and HTML5 data storage.
7. Improper Session Handling
Improper session handling alludes to the continuation of the session for an extensive period of time, even when the user has switched from the app. A number of e-Commerce mobile apps prefer enabling longer sessions to speed up the buying process and other business does as such to provide superior user experience by upgrading the speed. However, this practice can be hazardous especially if the phone gets stolen. Anybody who gets access to the device can take control of the application and steal important information.
The most ideal approach to locate a middle ground between speed and security protection is to utilize re-authentication for important activities like buys or access to priority marked documents. In this way, you will let users have the imperative access without compromising on mobile application security.
8. Poor Authentication
Poor or missing authentication enables a hacker to namelessly access the mobile application or backend server of the app.
The internet connections of mobiles are not very reliable as the internet connections over websites, which implies that mobile applications may require offline authentication to look after uptime.
App Developers must know that these prerequisites can make security loopholes. In their offline mode, applications are generally more vulnerable. They can enable users with low authorizations to execute actions entitled only to admins. Hence, it’s smarter to restrain logins in online mode.
After seeing the general mistakes that developers make which plague mobile app security, let us move on to the specifics about the Android and iOS mobile application security.
Also Read: 9+ Web Application Security Best Practices
How to Make Your Android App Safe?
By making your application secure, you can earn your user’s trust which in turn will boost your business. Below mentioned best practices will have a positive effect on your Android application’s security:
- Store Your User’s Data Securely
The most imperative thing in digital security is storing your user’s data securely. There are two ways of saving data on your device; internal storage and external storage. Here is a difference between both of these methods:
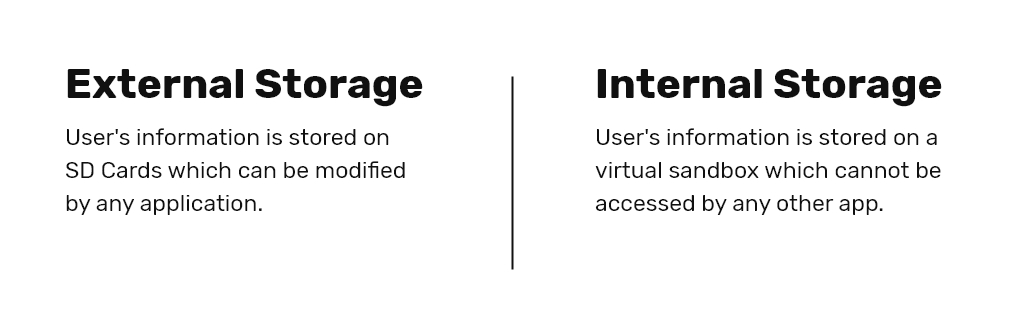
For better security, you shouldn’t use external storage in Android for storing your user’s data as it can be used or modified by some other app from there. On the other hand, if your user’s data is saved internally, the user can set encryption on it by setting a password. Then again, this password isn’t directly stored in the memory of the device. When a user enables this encryption it secures the key components of the OS.
- Permission in Android OS
Sandbox system requests user’s authorization for every interaction between the applications. Thus, if you want your Android application to be friendly, coders should implement this function utilizing a sandbox framework that is secure and safe. It also ensures that applications don’t collect your data and don’t utilize an excessive number of resources.
- Use HTTPS
The entire communication that happens between the application and the server should be over an HTTPS connection. Various Android Users are often connected with many open WiFi networks in public areas and utilizing HTTP rather than HTTPS can leave the device helpless against numerous malicious hotspots that can easily modify the content of HTTP traffic and can make the mobiles application behave in an unexpected manner.
- Using GCM instead of SMS
At the time when GCM or Google Cloud Messaging didn’t exist, SMS was utilized so as to drive data from servers to applications however today, we use GCM. But, if you haven’t changed from SMS to GCM yet, you should. This is because SMS protocol is neither encrypted nor safe.
So, that was all about how you can make your Android app safe. While there are other security practices as well that includes validation of user input and use of ProGuard before you publish your app, the above-mentioned ways are a must-have for the security.
Now, that we know what we need to do to ensure the safety of an Android app, let’s see what iOS apps need to be secure.
How to Make Your iOS App Safe?
iOS, because of its security systems and restrictions by Apple, is viewed as one of the most secure mobile OSs. However, this doesn’t mean that you can neglect security when building up an iOS application.
Potential Security hazards in iOS include “data breaks” and “Man in the middle attack.” Here are some best practices that will enable you to make secure iOS applications for your users:
- KeyChain API For the Storage of Data
To save sensitive data in iOS applications, we should utilize security services provided by Apple. Keychain service API helps you take care of security issues by giving your application an approach to store the small amount of user data in an encoded database called the keychain.
In the keychain, you are allowed to save passwords and other secrets that the user cares about, for example, card information or even short notes.
- Networking security
Apple is known for its privacy policies and strategies. A couple of years back, Apple had presented App Transport Security which implements third-party mobile applications to send network requests over an increasingly secure connection, i.e., HTTPS.
- SSL Pinning
SSL Pinning is a procedure that enables us to deal with an attack called Man in the Middle. SSL depends on the certificate’s “chain of trust”. At the point when communication begins, it is checked whether the server’s SSL certificate is trusted by any SSL Certificate Authority or not.
We can utilize SSL Pinning to guarantee that the application communicates with the assigned server itself. This can be done by saving the SSL certificate of the target server inside the application bundle.
Even following these means doesn’t mean your application is 100% insusceptible. There is an unceasing war among app developers and hackers. But, as an app developer, you should take every single precaution to guarantee the safety of your iOS as well as Android App. I hope the above-mentioned points will help you in the same!
Wrapping Up
Making an app secure is a task that should be taken care of during app development NYC and should never be neglected even after the app launches and becomes successful. In this article, we have discussed the common mistakes that developers make while building an app and ways to avoid them. In the second section, we have seen some platform-oriented best practices for building secure apps.
If you need further assistance on securing your mobile app, you can contact our experts at Apptunix.
Rate this article!
(2 ratings, average: 5.00 out of 5)
Join 60,000+ Subscribers
Get the weekly updates on the newest brand stories, business models and technology right in your inbox.

Nikhil Bansal is the Founder and CEO of Apptunix, a leading Software Development Company helping startups as well as brands in streamlining their business processes with intuitive and powerful mobile apps. After working in the iOS app development industry for more than 10 years, he is now well-equipped with excellent problem-solving and decision-making techniques.

Telemedicine 2.0 - A Comprehensive Guide On What Healthcare Providers Need To Know?
Discover how the latest advancements like Artificial Intelligence in telemedicine are reshaping patient care. This comprehensive resource offers insights into the key trends and innovations driving this shift, providing valuable knowledge for healthcare professionals looking to stay ahead.
Download Now!Don't Know Much
About Technology?
Let our experts help you decide the right tech stack for your idea.



















